It’s Time for Govcon to Comply with New Cybersecurity Model
By Kim Koster
One of the many lessons to come out of the ongoing global health crisis is that, even amid quarantines, stay-home orders, and a drastic slowdown in business and economic activity, cyber threats never rest — and in some instances, even escalate.
The Covid-19 CTI League, an ad hoc group of security experts that is working to neutralize cyber threats during the pandemic, recently hammered that lesson home, saying “the amount of COVID-19 related cyberattacks is surging,” with widespread reports of “suspicious domains, compromised infrastructures, and other cyber-attacks by malicious actors.”
The persistence of cybercrime during the coronavirus pandemic hasn’t been lost on the U.S. Department of Defense (DoD). As of late June, the agency appeared intent to keep to its aggressive schedule for implementing a new set of tighter cybersecurity standards that defense contractors must meet in order to be considered for DoD contracts.
While the new standards included in DoD’s Cybersecurity Maturity Model Certification (CMMC) program were unveiled in January 2020, before the coronavirus tightened its grip, indications are that rollout of the standard will continue apace. Even as the COVID-19 crisis has forced DoD to delay the pending DFARS rule change that would make CMMC the standard for government contractor cybersecurity, the agency is committed to moving forward with its ambitious timeline for implementing CMMC and building out the infrastructure to support it.
Observers who have been closely tracking development and implementation of the CMMC say they expect the first RFIs (requests for information) with the CMMC requirement to be issued sometime this summer (delayed from late spring), while RFPs with the CMMC requirement are likely to be issued starting in late fall or early winter 2020, provided conditions related to the pandemic don’t cause further delays.
Although as of this writing, no individuals or entities had been approved to certify government contractors to the new CMMC standard, officials from Cherry Bekaert, a firm that advises government contractors on their compliance programs, are strongly recommending that contractors that do business with the DoD immediately begin the compliance process, particularly if they want to gain CMMC certification by the end of 2020.
“The lack of accredited certifying bodies shouldn’t stop organizations from taking necessary steps now to get where they need to be,” Neal W. Beggan, Principal, Risk Assurance and Advisory Services at Cherry Bekaert, told the audience during a recent webcast about CMMC. Recent guidance from DoD suggests the certification process will take at least six months, he noted.
2020 Wash100 Award recipient Katie Arrington, who leads the CMMC effort for the DoD as the Chief Information Security Officer for the agency’s acquisition office, recently announced that the department had taken another important step in formalizing CMMC by entering into a Memorandum of Understanding to empower the non-profit, independent CMMC Accreditation Board (CMMC AB) to train and certify the third-party assessors who will verify government contractor compliance with CMMC. The DoD has assigned the National Institute of Standards and Technology (NIST) to help create requirements for those assessors.
While the DoD, the CMMC AB, and NIST are busy with those responsibilities, government contractors impacted by the CMMC have plenty on their plates, too, if they want to do business with DoD, starting with gaining an understanding of how CMMC will work. CMMC Version 1.0 details a unified cybersecurity standard with practices and processes that the roughly 300,000 entities within the Defense Industrial Base must meet in order to work with the DoD. The new standards apply to primary DoD contractors as well as their subcontractors.
The CMMC model is designed to protect sensitive information along the DoD supply chain. It prescribes best practices to which contractors must document adherence in order to get CMMC-certified to one of the framework’s five levels of cybersecurity. Those levels include Basic, Intermediate, Good, Proactive, and Advanced/Progressive.
Levels 1, 2, and 3 are based largely on the NIST 800-171 standard. All DoD government contractors will be required to get certified to at least Level 1. Government contractors that manage controlled unclassified information (CUI) will be required to meet the requirements of Level 3. The vast majority of contractors are expected to require certification to levels 1, 2, or 3, with less than 1% required to be certified to Level 4 and a similar percentage requiring certification to Level 5.
“The CMMC model (detailed in the graphics below) includes 17 domains of capabilities and a total of 171 practices across the five maturity levels, ranging from basic cyber hygiene to sophisticated, proactive measures,” Steven J. Ursillo, Jr., Partner and National Leader of Information Assurance for Cherry Bekaert, explained during the webcast.
CMMC Maturity Process Progression
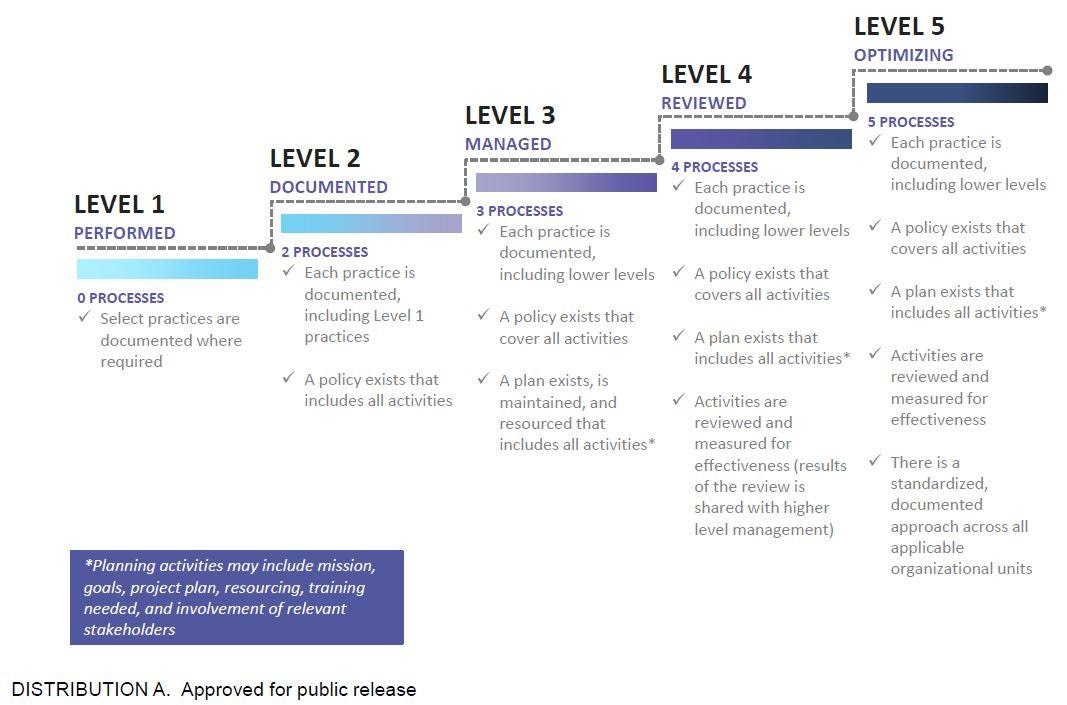
CMMC Maturity Practice Progression
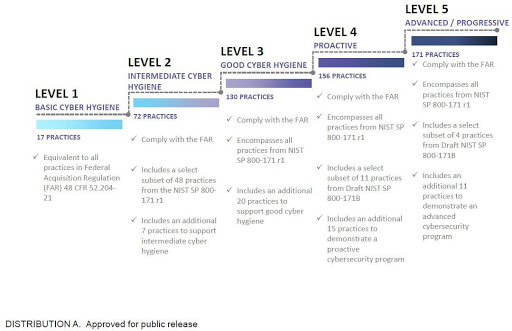
During the certification process, CMMC AB assessors will evaluate organizations on both the process and practice spectrums, Ursillo said. So if, for example, an organization is deemed to meet the Level 3 requirements for good hygiene but lacks the process documentation expected for that level, it would default back to Level 2 certification.
With the CMMC AB busy training its assessors so the daunting task of evaluating some 300,000 contractor cybersecurity programs can begin, DoD contractors have a window in which to start preparing for CMMC compliance. Below are the steps they could — and according to the Cherry Bekaert officials, should — be taking now:
- Gain a thorough understanding of CMMC requirements.
- Start internally identifying the scope of work for complying with CMMC.
- If your company currently lacks a cyber security program and expects to seek business from DoD as a prime contractor or subcontractor, begin the process of formalizing a program.
- If you have a cyber program but are not currently following or implementing it, engage key stakeholders in your company, as well as trusted advisors, to identify the necessary steps to implement the program. Be sure company leadership is onboard with the program.
- Identify the maturity level to which your company will seek certification, based on the level of work your company expects (or aspires) to provide.
- If your company relies on third-party providers for risk management, assess your company’s vendor risk management program and consider formalizing the program to include relevant certifications and attestations to demonstrate vendor/provider compliance. If your firm utilizes large subcontractors to fulfill DoD contracts, gauge the maturity of their cyber programs relative to CMMC.
- Conduct a pre-assessment/readiness assessment (perhaps enlisting a certified third-party assessor organization, or C3PAO) to identify any potential gaps in your company’s cyber security practices and processes relative to the level of certification you expect to seek.
- Work to fill any gaps identified in the pre-assessment.
- Be sure to track costs related to complying with CMMC, as DoD recently said those costs will be recoverable, according to Beggan.
- Consider utilizing a GRC (governance, risk & compliance) software platform and/or control repositories to streamline the process.
Amid the many lingering questions about how the CMMC certification process will unfold, one thing is certain: an ERP system with robust, customizable tracking and reporting tools can simplify and expedite the compliance process for government contractors seeking any level of CMMC certification. That process likely will begin in earnest very soon.
Kim Koster is Vice President of GovCon Strategy for Unanet, focusing on project management, accounting and government contracting. Unanet, a leader in ERP software purpose-built for government contractors, has been following the CMMC process closely and is well-positioned to assist government contractors in their efforts to comply with the policy, having integrated capabilities into the Unanet software platform to support the relevant technical requirements within the new CMMC model. For an in-depth, look at CMMC, check out our free white paper here.















